Compliance Checker
The Compliance Checker is a Security Content Automation Protocol (SCAP) based engine that provides compliance audit functionality for a target Vblock System. The Compliance Checker, which you can access using the Plug-in for vCenter, provides a set of criteria that determines Vblock System compliance with a specific content pack.
Available compliance content packs
The Compliance Checker uses the following content packs to assess Vblock System compliance:
- Vblock System Release Certification Matrix (RCM)
RCMs define software, firmware, and hardware that VCE tests and validates as supported for a Vblock System.
You can run compliance scans against an RCM to easily identify Vblock System compliance with that RCM. - VCE security hardening guidelines (Security Compliance Validation)
VCE security hardening guidelines optionally provide security best practices that help you identify risks that might exist on the Vblock System. The scan uses the VCE security standards described in the VCE Vblock System Security Guide: Configuration. - VCE Security Alert (VSA) and VCE Technical Alert (VTA)
The VSA and VTA content packs provide targeted, specific technical alerts or vulnerabilities that VCE have identified for particular Vblock System components.
The VSA enables you to rapidly identify and remediate security vulnerabilities while the VTA enables you to quickly assess and resolve technical issues.
Note: If your Vblock System contains optional components, they are not included in compliance scans by default. Refer to the Plug-in for vCenter online help for more information on including optional components in compliance scans.
Updating compliance content
You should update compliance content to the most recent version so that the Compliance Checker is up to date when you run compliance scans on your Vblock System. Compliance content includes rules for Release Certification Matrices (RCM), security hardening, and VCE Technical Alerts compliance.
Download the RPM Package Manager (RPM) file that contains the updated compliance content you plan to install.
To access RPM files, log in to the VCE Support site, VCE Download Center and then navigate to the ‘VCE™ Software and VCE™ Software Documentation for VCE™ Converged Infrastructure Systems‘.
- Copy the RPM file(s) to any location on the VCE Vision virtual machine.
- Change to the directory that contains the RPM file(s).
- Run
rpm -Uvh content_rpm_name-build_number.rpmto save the compliance content in the following location:/opt/vce/compliance/content/content_subdirectory.[root@vio001 conf]# cd /tmp [root@vio001 tmp]# rpm -Uvh vce-compliance-content-2.6.0.0-2015.03.00.x86_64.rpm Preparing... ########################################### [100%] 1:vce-compliance-content ########################################### [100%] Compliance API version is 2.6.2.0 [root@vio001 tmp]# rpm -Uvh vce-compliance-content-techalert-2.6.0-2015.04.00.x86_64.rpm Preparing... ########################################### [100%] 1:vce-compliance-content-########################################### [100%]
- Install the compliance content:
- Change directory to: cd /opt/vce/compliance/content
[root@vio001 tmp]# cd /opt/vce/compliance/content
- Install the compliance content by running the following command:
sh install_content.sh. You will be prompted to type admin’s password.[root@vio001 content]# sh install_content.sh Enter CAS password for admin user: <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01 Transitional//EN" "http://www.w3.org/TR/html4/loose.dtd"> <html> <head> <meta http-equiv="Content-Type" content="text/html; charset=UTF-8"> <title>VCE Vision(TM) Compliance Checker</title> </head> <body> <h4>The VCE Vision™ Compliance Checker has been successfully installed</h4> <!-- <a href="index.html">Documentation</a> --> </body> </html> ** Installing content from /opt/vce/compliance/content/rcm... Importing RCM Content for VCE Vblock(TM) System 540... Import Successful ** Setting the version for RCM Content for VCE Vision(TM) Compliance Checker... ** Installing content from /opt/vce/compliance/content/techalert... Importing VCE Technical Alert Content for VCE Vblock(TM) System 540... Import Successful ** Setting the version for Technical Alerts for VCE Vision(TM) Compliance Checker... ################################################## CONTENT INSTALL RESULTS Successfully imported content: ------------------------------ RCM Content for VCE Vblock(TM) System 540 VCE Technical Alert Content for VCE Vblock(TM) System 540 ##################################################
- Change directory to: cd /opt/vce/compliance/content
- You can now refresh Vblock Compliance Policies in the vSphere Web Client:
Home – Vblock System – Select Vblock – Manage tab – Compliance – Policies
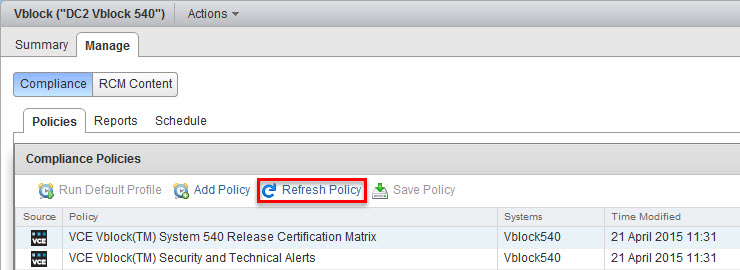
Check Vblock RCM compliance:
- Highlight RCM policy and select compliance profile from the bottom list and click on Run Scan:

Click Yes to confirm - Navigate to the Reports tab to view the results of the scan
- Wait for the scan status to change to COMPLETED and check the Score
- Click on Compliance Report to view compliance scan details.
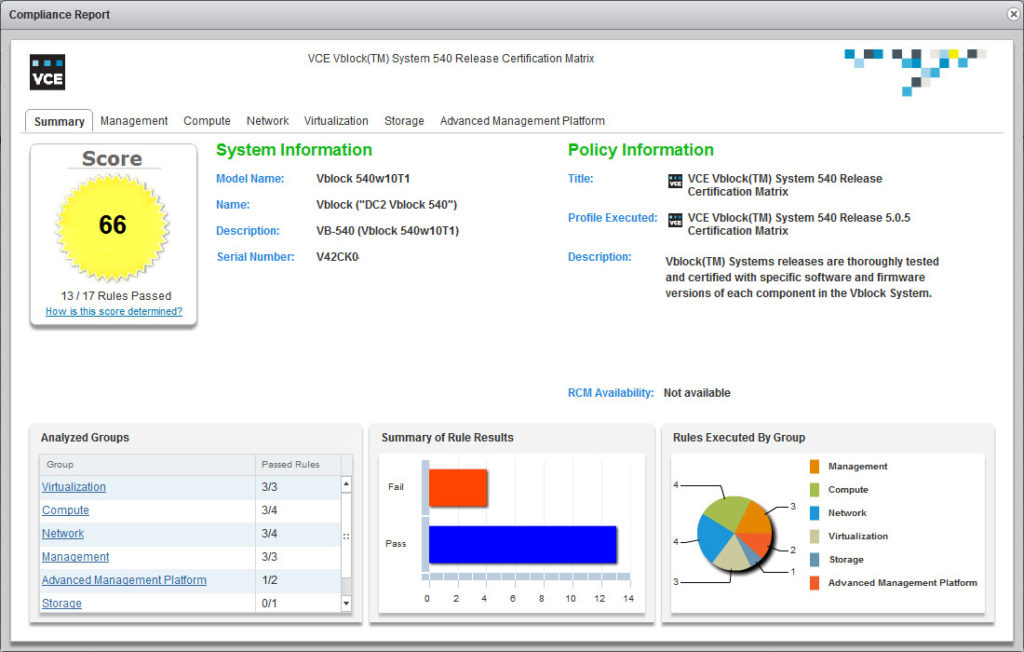
- You may also go through the tabs to view more detailed information about a selected components. When you select an item from the list of items tested, you can see the actual values of each item, including any expected values
Here are a couple of examples:- The compliance checker picked up that the Cisco UCS CNA firmware version is not as expected:
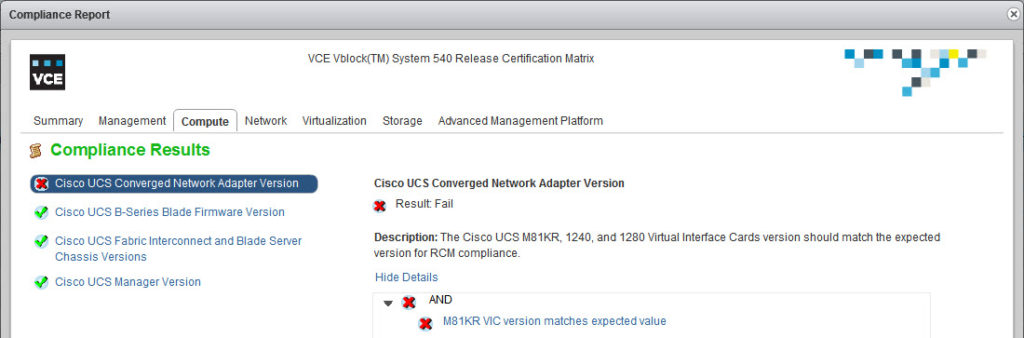
Well, that is not exactly true:- VCE RCM 5.0.5 specifies the following:
Compute
Cisco UCS Converged Network Adapters: Cisco UCS 1240, 1280, 1340, and 1380 Virtual Interface Cards
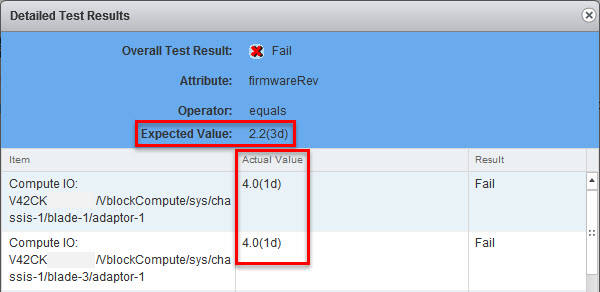
Version certified: in Cisco UCS Manager 2.2(3d)
“in” Cisco UCS Manager 2.2(3d) does not mean the firmware version must be 2.2(3d)! - Login to UCS Manager and check CNA firmware version that comes with 2.2(3d):
Cisco UCS M81KR – 2.2(3b)
Cisco UCS VIC 1240, 1340, 1280 and 1380 – 4.0(1d)
- VCE RCM 5.0.5 specifies the following:
- Cisco Nexus 1000v is missing…
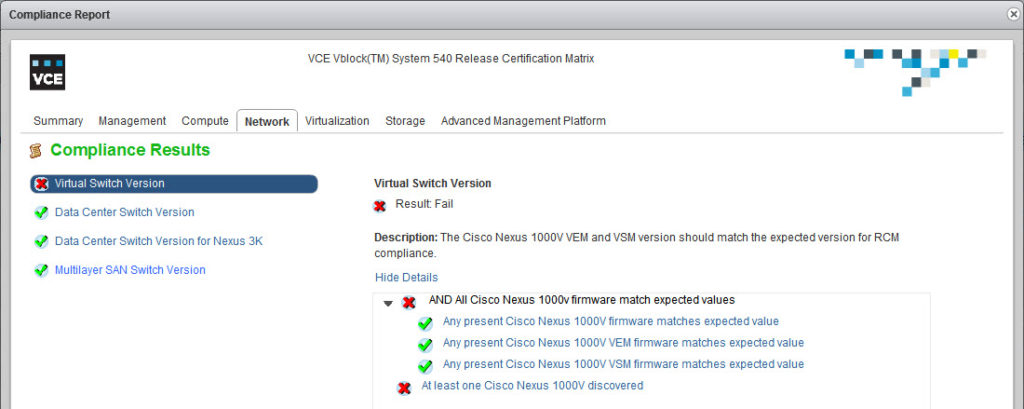
This is actually an expected behavior as this particular Vblock does not have Cisco Nexus 1000v…
- The compliance checker picked up that the Cisco UCS CNA firmware version is not as expected:
Customize the Compliance Checker to reflect your environment
VCE provides you with a set of pre-defined policies and profiles. To customize the Compliance Checker to reflect your environment, use the Profile Tailoring feature.
Profile Tailoring allows you to take an existing compliance policy and tailor it to your environment. The new policies are saved, evaluated, and reported on as if they were the original policies.
A policy is a compliance policy that contains information about what to check in the environment. You can add a new policy, save a policy, or delete it. You cannot edit or delete any policy that VCE provides. However, a policy can have one or more profiles.
A profile is a grouping of rules to audit and the desired target values according to VCE standards.
You define a new profile to specify the rules that reflect your environment. Any profile you create can be edited, saved, and deleted. You can copy a VCE-created profile (they can be identified by the VCE logo in the Source column) to make a change for that profile to fit your environment. Any profile that is created by VCE cannot be edited or deleted. You can select a profile and run a scan from the Profiles area on the compliance policies page.
- Create a copy of the compliance profile:
- Run the compliance scan against the custom profile.
The same procedure is also applicable to the Security and Technical Alerts compliance policy as well.

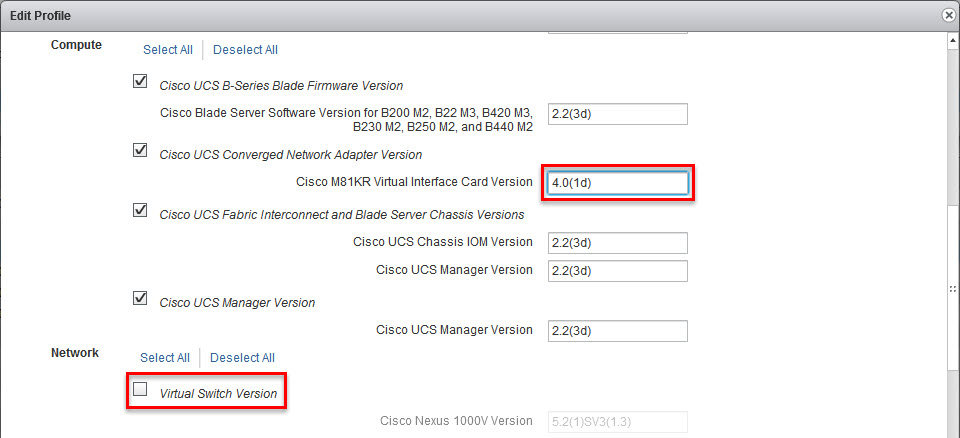
How to check RCM version